Web / SNMP MANAGEABLE
SGSW-2403
24-Port 10/100/1000Mbps stackable switch
6.1 Web-Based Configuration and Monitoring
As well as the menu-driven system configuration program, the agent module provides an embedded HTTP Web agent. This agent can be accessed by any computer on the network using a standard Web browser (Internet Explorer 4.0 or above, or Netscape Navigator 4.0 or above).
Using the Web browser management interface you can configure a switch and view statistics to monitor network activity. The Web interface also provides access to a range of SNMP management functions with access to the switch's MIB and RMON database.
Prior to accessing the switch from a Web browser, be sure you have first performed the following tasks:
6.2 Navigating the Web Browser Interface
To access the Web-browser interface you must first enter a user name and password. The default user name is "admin" with no password. The administrator has Read/Write access to all configuration parameters and statistics.
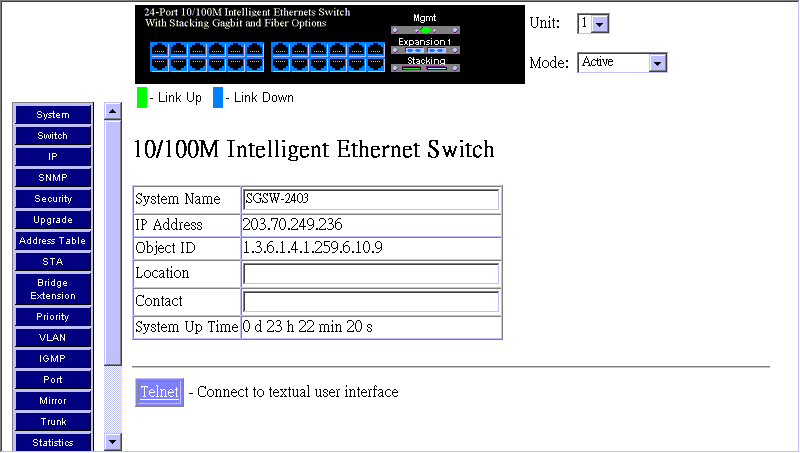
When your Web browser connects with the switch´s Web agent, the home page is displayed as shown below. The home page displays the Main Menu on the left-hand side of the screen and System Information on the right-hand side. The Main Menu links are used to navigate to other menus and display configuration parameters and
If this is your first time to access the
management agent, you should define a new Administrator password, record it
and put it in a safe place. From the Main Menu, select Security and enter a
new password for the Administrator. Note that passwords can consist of up to
11 alphanumeric characters and are not case sensitive.
NOTES: |
Based on the default configuration, a user is allowed three attempts to enter the correct password; on the third failed attempt the current connection is terminated. See "Console Login Configuration". |
Configurable parameters have a dialog box or
a drop-down list. Once a configuration change has been made on a page, be sure
to click on the "Apply" button at the bottom of the page to confirm
the new setting. The following table summarizes the Web page configuration buttons.
Web Page Configuration Buttons |
|
Button |
Action |
Apply |
Sets specified values in the management agent. |
Revert |
Cancels specified values prior to pressing the ¤Apply?button. |
Refresh |
Immediately updates values from the management agent. |
Help |
Provides help on using the Web management interface. |
NOTES: |
|
The Web agent displays an image of the switch´s ports, showing port links and activity. Clicking on the image of a port displays statistics and configuration information for the port. Clicking on the image of the serial port (labeled "Mgmt" displays the Console Configuration screen. Clicking on any other part of the front panel displays "Switch Information".
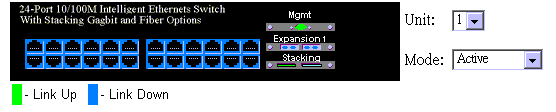
Click on any port to display a summary or port status as shown below, as well as
Etherlike statistics and RMON
statistics.
Parameter |
Description |
|
Type |
Shows port type as: |
|
10/100TX |
: 10BASE-T / 100BASE-TX |
|
100FX |
100BASE-FX |
|
1000SX |
1000BASE-SX |
|
Admin Status |
Shows if the port is enabled, or has been disabled due to abnormal behavior or for security reasons. See "Port Configuration". |
|
Link Status |
Indicates if the port has a valid connection to an external device. |
|
Speed Status |
Indicates the current port speed. |
|
Duplex Status |
Indicates the port´s current duplex mode. |
|
Flow Control Status |
Shows the flow control type in use. Flow control can eliminate frame loss by "blocking" traffic from end stations connected directly to the switch. |
|
VLAN |
The VLAN ID assigned to untagged frames received on this port. You can set the default Port VLAN ID (PVID) under "VLAN Port Configuration" to assign ports to the same untagged VLAN. |
|
If you are having difficulties making an out-of-band console connection to the serial port on the agent module, you can display or modify the current settings for the serial port through the Web agent. Click on the serial port icon in the switch image to display or configure these settings, as shown below.
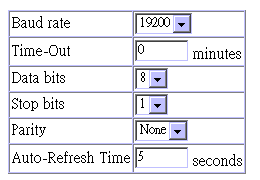
Parameter |
Default |
Description |
Baud rate |
19200 bps |
The rate at which data is sent between
devices. |
Time-Out |
10 minutes |
If no input is received from the attached
device after this interval, the current session is automatically
closed. |
Data bits |
8 bits |
Sets the data bits of the RS-232 port. |
Stop bits |
1 bit |
Sets the stop bits of the RS-232 port. |
Parity |
none |
Sets the parity of the RS-232 port. |
Auto-Refresh Time |
5 seconds |
Sets the interval before a console session
will auto refresh the console information, such as Spanning
Tree Information, Port Configuration, Port Statistics, and RMON
Statistics. |
Using the on-board Web agent, you can define system parameters, manage and control the switch, the connected stack and all its ports, or monitor network conditions. The following table briefly describes the selections available from this program.
Menu |
Description |
|
System |
Provides basic system description, including contact information. |
|
Switch |
Shows hardware/firmware version numbers, power status, and expansion modules in use. |
|
IP |
Includes boot state, IP address, and the maximum number of Telnet sessions allowed. |
|
SNMP |
Configures communities and trap managers; and activates traps. |
|
Security |
Sets password for system access. |
|
Upgrade |
Downloads new version of firmware to update your system. |
|
Address Table |
Provides full listing of unicast addresses, sorted by address or VLAN. |
|
STA |
Enables Spanning Tree Algorithm; also sets parameters for switch priority, hello time, maximum message age, and forward delay; as well as port priority and path cost. |
|
Bridge Extension |
Displays/configures extended bridge capabilities provided by this switch, including support for traffic classes and VLAN extensions. |
|
Priority |
Configures default port priorities and displays queue assignments. |
|
VLAN |
Configures VLAN group members and other port-specific VLAN settings. |
|
IGMP |
Configures IGMP multicast filtering. |
|
Port |
Enables any port, sets communication mode to auto-negotiation, full duplex or half duplex, and enables/disables flow control. |
|
Mirror |
Sets the source and target ports for mirroring. |
|
Trunk |
Specifies ports to group into aggregate trunks. |
|
Statistics |
Displays statistics on network traffic passing through the selected port. |
|
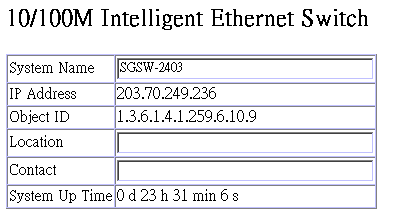
Use the System Information screen to display descriptive information about the switch, or for quick system identification as shown in the following figure and table.
Parameter |
Description |
System Name* |
Name assigned to the switch system. |
IP Address |
IP address of the agent you are managing. The agent supports SNMP over UDP/ IP transport protocol. In this environment, all systems on the Internet, such as network interconnection devices and any PC accessing the agent (or running SNMPc) must have an IP address. Valid IP addresses consist of four numbers, of 0 to 255, separated by periods. Anything outside of this format will not be accepted by the configuration program. |
Object ID |
MIB II object identifier for switch´s network management subsystem. |
Location* |
Specifies the area or location where the system resides. |
Contact * |
Contact person for the system. |
System Up Time |
Length of time the current management agent has been running. |
* Maximum string length is 255, but the screen only displays 45 characters. You can use the arrow keys to browse the whole string.
Use the Switch Information screen to display hardware/firmware version numbers for the main board, as well as the power status and modules plugged into the system.

Parameter |
Description |
Serial Number |
Serial number of the main board. |
Number of Ports |
Number of built-in ports. |
Hardware Version |
Hardware version of the main board. |
Firmware Version |
System firmware version in ROM. |
Internal Power Status |
Power status for the switch. |
Redundant Power Status |
Redundant power status for the switch. |

Parameter |
Description |
Hardware Version |
Hardware version of the Agent Module. |
POST ROM Version |
Agent Module´s Power-on Self-test version. |
Firmware Version |
Agent Module´s firmware version. |
Role |
Shows if this module is Master or Slave. |
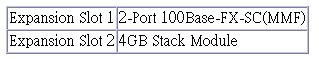
Parameter |
Description |
Expansion Slot 1 |
Shows module type if inserted (100BASE-FX or 1000BASE-SX). |
Expansion Slot 2 |
Shows module type if inserted (100BASE-FX, 1000BASE-SX, or 4GB Stack).. |
Use the IP Configuration screen to set the bootup option, configure the IP address for the on-board management agent, or set the number or concurrent Telnet sessions allowed. The screen shown below is described in the following table.
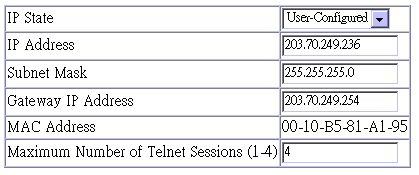
Parameter |
Default |
Description |
IP State |
USER-CONFIG |
Specifies whether IP functionality is
enabled via manual configuration, or set by Boot Protocol (BOOTP).
Options include: |
IP Address |
10.1.0.1 |
IP address of the switch you are managing. The switch supports SNMP over UDP/IP transport protocol. In this environment, all systems on the Internet, such as network interconnection devices and any PC accessing the on-board agent (or running AccView) are assigned an IP address. Valid IP addresses consist of four numbers, of 0 to 255, separated by periods. Anything outside of this format will not be accepted by the configuration program. |
Subnet Mask |
255.255.0.0 |
Subnet mask of the switch you have selected. This mask identifies the host address bits used for routing to specific subnets. |
Gateway IP |
|
Gateway used to pass trap messages from the switch to the management station. Note that the gateway must be defined if the management station is located in a different IP segment. |
MAC Address |
|
Physical address of the agent module. |
Number of Telnet sessions |
4 |
Sets the number of concurrent Telnet
sessions allowed to access the agent. |
Use the SNMP Configuration screen to display and modify parameters for the Simple Network Management Protocol (SNMP). The stack should include an SNMP agent module which monitors the status of its hardware, as well as the traffic passing through its ports. A computer attached to the network, called a Network Management Station (NMS), can be used to access this information. Access rights to the agent module are controlled by community strings. To communicate with the switch, the NMS must first submit a valid community string for authentication. The options for configuring community strings and related trap functions are described in the following figures and table.
The following figure and table describe how to configure the community strings authorized for management access. Up to 5 community names may be entered.

Parameter |
Description |
SNMP Community Capability |
Up to 5 community strings may be used. |
Community String |
A community entry authorized for management access. (The maximum string length is 20 characters.) |
Access Mode |
Management access is restricted to Read Only or Read/Write. |
Add/Remove |
Add/remove strings from the active list. |
The following figure and table describe how to specify management stations that will receive authentication failure messages or other trap messages from the switch. Up to 5 trap managers may be entered.

Parameter |
Description |
Trap Manager Capability |
Up to 5 trap managers may be used. |
Trap Manager IP Address |
IP address of the trap manager. |
Trap Manager Community String |
A community authorized to receive trap messages. |
Add/Remove |
Add/remove strings from the active list. |
Enable Authentication Traps |
Issues a trap message to specified IP
trap managers whenever authentication of an SNMP request fails. |
Use the Security Configuration screen to restrict management access based on a specified password. The Administrator has write access for parameters governing the SNMP agent. You should therefore assign a password to the Administrator as soon as possible, and store it in a safe place. (If for some reason your password is lost, or you cannot gain access to the system´s configuration program, contact your PLANET distributor for assistance.)
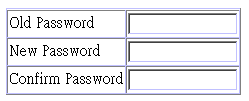
This password is for the system Administrator, with access privilege of Read/Write
for all screens. Passwords can consist of up to 11 alphanumeric characters and
are not case sensitive. (The defaults are: User name: admin; password: null)
You can upgrade system firmware via a Web browser, a TFTP server, or a direct connection to the console port.
Use the Web Upload Management menu to load software updates into the switch. The upload file should be a binary file from PLANET; otherwise the agent will not accept it. The success of the upload operation depends on the quality of the network connection. After uploading the new software, the agent will automatically restart itself. Parameters shown on this screen are indicated in the following figure and table.
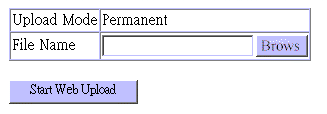
Parameter |
Description |
Upload Mode |
Uploads to permanent flash ROM. |
File Name |
The binary file to download. Use the Browse button to locate the file on your local network. |
Start Web Upload |
Starts uploading the file over the network. |
6.A.2 TFTP Download Management
Use the TFTP Download Management menu to load software updates into the switch. The download file should be a binary file from PLANET; otherwise the agent will not accept it. The success of the download operation depends on the accessibility of the TFTP server and the quality of the network connection. After downloading the new software, the agent will automatically restart itself. Parameters shown on this screen are indicated in the following figure and table.

Parameter |
Description |
Server IP Address |
IP address of a TFTP server. |
Download Mode |
The system downloads to permanent flash ROM. |
File Name |
The binary file to download. |
Start TFTP Download |
Issues request to TFTP server to download the specified file. |
6.B Address Table Configuration
The Address Table contains the unicast MAC addresses and VLAN identifier associated with each port (that is, the source port), sorted by MAC address or VLAN. You can also clear the entire address table, or information associated with a specific address; or set the aging time for deleting inactive entries. The information displayed in the Address Table is indicated in the following figure and table.

Parameter |
Description |
Aging Time |
Time-out period in seconds for aging
out dynamically learned forwarding information. |
Dynamic Address Count |
The number of dynamically learned addresses. |
Static Address Count |
The number of statically configured addresses. |
Address Table Sort by |
Entries can be sorted by address or VLAN ID. |
Address Table |
The system displays the MAC address of each node, and the port whose address table includes this MAC address, the associated VLAN(s), and the address status (i.e., dynamic or static). |
New Static Address |
Use these fields to add or remove a static entry to the address table. Indicate the address, stack unit, port and VLAN group when adding a new entry. |
Add/Remove |
Adds/removes the selected address. |
Clear Table |
Removes all addresses from the address table. |
6.C Spanning Tree Algorithm (STA)
The Spanning Tree Algorithm can be used to detect and disable network loops, and to provide backup links between switches, bridges or routers. This allows the switch to interact with other bridging devices (that is, STA compliant switch, bridge or router) in your network to ensure that only one route exists between any two stations on the network. For a more detailed description of how to use this algorithm, refer to "Spanning Tree Algorithm" .
6.C.1 Spanning Tree Information
The Spanning Tree Information screen displays a summary of the STA information for the overall bridge or for a specific port. To make any changes to the parameters for the Spanning Tree, use the Spanning Tree Configuration menu.
The parameters shown in the following figure and table describe the current bridge STA Information.
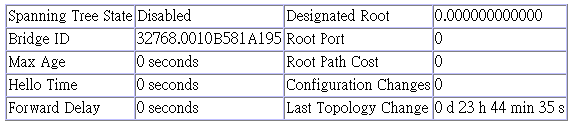
Parameter |
Description |
Spanning Tree State |
Shows if the switch is enabled to participate in an STA compliant network. |
Bridge ID |
A unique identifier for this bridge, consisting of bridge priority plus MAC address (where the address is normally taken from the agent). |
Max Age |
The maximum time (in seconds) a device can wait without receiving a configuration message before attempting to reconfigure. |
Hello Time |
The time interval (in seconds) at which the root device transmits a configuration message. |
Forward Delay |
The maximum time (in seconds) the root device will wait before changing states (i.e., listening to learning to forwarding). |
Designated Root |
The priority and MAC address of the device in the spanning tree that this switch has accepted as the root device. |
Root Port |
The number of the port on this switch that is closest to the root. This switch communicates with the root device through this port. If there is no root port, then this switch has been accepted as the root device of the spanning tree network. |
Root Path Cost |
The path cost from the root port on this switch to the root device. |
Configuration Changes |
The number of times the spanning tree has been reconfigured. |
Last Topology Change |
The time since the spanning tree was last reconfigured. |
The parameters shown in the following figure
and table are for port STA Information.
Port |
Port Status |
Forward Transitions |
Designated Cost |
Designated Bridge |
Designated Port |
1 |
Broken |
0 |
5011 |
32768.0010B54C1EB6 |
128.1 |
2 |
Broken |
0 |
5011 |
32768.0010B54C1EB6 |
128.2 |
3 |
Broken |
0 |
5011 |
32768.0010B54C1EB6 |
128.3 |
4 |
Broken |
0 |
5011 |
32768.0010B54C1EB6 |
128.4 |
5 |
Forwarding |
1 |
4992 |
32769.2000E8003889 |
0.6 |
6 |
Broken |
0 |
5011 |
32768.0010B54C1EB6 |
128.6 |
7 |
Broken |
0 |
5011 |
32768.0010B54C1EB6 |
128.7 |
8 |
Broken |
0 |
5011 |
32768.0010B54C1EB6 |
128.8 |
9 |
Broken |
0 |
5011 |
32768.0010B54C1EB6 |
128.9 |
10 |
Broken |
0 |
5011 |
32768.0010B54C1EB6 |
128.10 |
11 |
Broken |
0 |
5011 |
32768.0010B54C1EB6 |
128.11 |
12 |
Broken |
0 |
5011 |
32768.0010B54C1EB6 |
128.12 |
Parameter |
|
Description |
Port Status |
Displays the current state of this port within the spanning tree: |
|
Broken |
No link has been established on this port. |
|
Disabled |
Port has been disabled by the user or has failed diagnostics. |
|
Blocked |
Port receives STA configuration messages, but does not forward packets. |
|
Listening |
Port will leave blocking state due to topology change, starts transmitting configuration messages, but does not yet forward packets. |
|
Learning |
Port has transmitted configuration messages for an interval set by the Forward Delay parameter without receiving contradictory information. Port address table is cleared, and the port begins learning addresses. |
|
Forwarding |
The port forwards packets, and continues learning addresses. |
|
The rules defining port status are:
|
||
Forward Transitions |
The number of times the port has changed status to forwarding state. |
|
Designated Cost |
The cost for a packet to travel from this port to the root in the current spanning tree configuration. The slower the media, the higher the cost. |
|
Designated Bridge |
The priority and MAC address of the device through which this port must communicate to reach the root of the spanning tree. |
|
Designated Port |
The priority and number of the port on the designated bridging device through which this switch must communicate with the root of the spanning tree. |
|
6.C.2 Spanning Tree Configuration
The following figures and tables describe Bridge STA configuration.
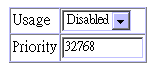
Parameter |
Default |
Description |
Usage |
Enabled |
Enable this parameter to participate in an STA compliant network. |
Priority |
32,768 |
Device priority is used in selecting
the root device, root port, and designated port. The device
with the highest priority becomes the STA root device. (Remember
that the lower the numeric value, the higher the priority.)
However, if all devices have the same priority, the device with
the lowest MAC address will then become the root device. |
6.C.2.2
When the Switch Becomes Root
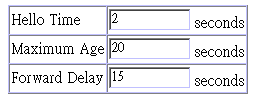
Parameter |
Default |
Description |
Hello Time |
2 |
The time interval (in seconds)
at which the root device transmits a configuration message. |
Max (Message) Age |
20 |
The maximum time (in seconds) a device
can wait without receiving a configuration message before attempting
to reconfigure. All device ports (except for designated ports)
should receive configuration messages at regular intervals.
Any port that ages out STA information (provided in the last
configuration message) becomes the designated port for the attached
LAN. If it is a root port, a new root port is selected from
among the device ports attached to the network. |
Forward Delay |
15 |
The maximum time (in seconds) the
root device will wait before changing states (i.e., listening
to learning to forwarding). This delay is required because every
device must receive information about topology changes before
it starts to forward frames. In addition, each port needs time
to listen for conflicting information that would make it return
to a blocking state; otherwise, temporary data loops might result. |
The following figure and table describe STA configuration for ports or modules.
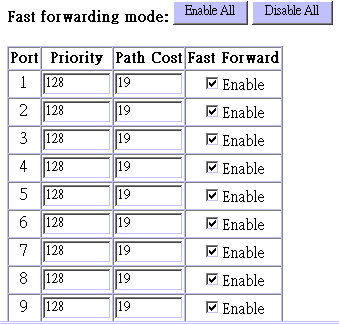
Parameter |
Default |
Description |
Fast Forwarding Mode (All Ports) |
Enabled |
See ¤Fast Forward?in this table.See ¤Fast Forward?in this table. |
Priority |
128 |
Defines the priority for the use of a
port in the STA algorithm. If the path cost for all ports on
a switch are the same, the port with the highest priority (i.e.,
lowest value) will be configured as an active link in the spanning
tree. Where more than one port is assigned the highest priority,
the port with lowest numeric identifier will be enabled. |
Path Cost |
100/19/4 |
This parameter is used by the STA algorithm
to determine the best path between devices. Therefore, lower
values should be assigned to ports attached to faster media,
and higher values assigned to ports with slower media. |
Fast Forward |
Enabled |
This enables/disables Fast Forwarding for the selected port. In this mode, ports skip the Blocked, Listening and Learning states and proceed straight to Forwarding. Fast Forwarding enables end-node workstations and servers to overcome time-out problems when the Spanning Tree Algorithm is implemented in a network. Therefore, Fast Forwarding should only be enabled for ports that are connected to an end-node device. |
6.D Configuring Bridge MIB Extensions
The Bridge MIB includes extensions for managed devices that support Traffic Classes and Virtual LANs. To display and configure these extensions, use the Bridge Extension screen as shown below:

Parameter |
Description |
Extended Multicast Filtering Services* |
Enables filtering of individual multicast addresses based on GMRP (GARP Multicast Registration Protocol). |
Traffic Classes |
This switch provides mapping of user priorities to multiple traffic classes. (Refer to the "Priority" ) |
Static Entry Individual Port |
This switch enables static filtering for unicast and multicast addresses. (Refer to the Address Table Configuration) |
VLAN Learning |
This switch uses Shared VLAN Learning (SVL), where the VLAN filtering database is shared among all ports. |
Configurable PVID Tagging |
This switch allows you to override the default PVID (Port VLAN ID) assigned to untagged incoming frames under VLAN Port Configuration. |
Local VLAN Capable* |
A local bridge (that is, dedicated Spanning Tree) is applied to each individual VLAN. |
* These functions are not available for the current firmware release.
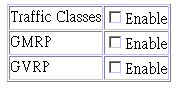
Parameter |
Description |
Traffic Classes* |
Multiple traffic classes are supported by this switch as indicated under Bridge Capabilities. However, this switch supports just two priority queues and only the default port priority can be configured. The switch does not support the configuration of traffic class mapping. Therefore, this parameter under Bridge Settings is set to disabled and cannot be enabled. |
GMRP* |
GARP Multicast Registration Protocol
(GMRP) allows network devices to register endstations with multicast
groups. |
GVRP* |
GARP VLAN Registration Protocol (GVRP) defines a way for switches to exchange VLAN information in order to register necessary VLAN members on ports across the network. This function should be enabled to permit VLANs groups which extend beyond the local switch. |
* These functions are not available for the current firmware release.
IEEE 802.1p defines up to 8 separate traffic classes. This switch supports Quality of Service (QoS) by using two priority queues, with Weighted Fair Queuing for each port. You can use the Priority Menu to configure the default priority for each port, or to display the mapping for the traffic classes.
6.E.1 Port Priority Configuration
Inbound frames that do not have any VLAN tags are tagged with the input port´s default VLAN ID (PVID) and the default ingress user priority as shown in the following screen, and then sorted into the appropriate priority queue at the output port. (Note that if the output port is an untagged member of the associated VLAN, these frames are stripped of all VLAN tags prior to transmission.)
The default priority for all ingress ports is zero. Therefore, any inbound frames that do not have priority tags will be placed in the low priority queue of the output port. You can use the Port Priority Configuration screen to adjust default priority for any port as shown below.

Parameter |
Description |
Port |
Numeric identifier for switch port. |
Default Ingress User Priority |
Default priority can be set to any value from 0~7, where 0~3 specifies the low priority queue and 4~7 specifies the high priority queue. |
Number of Egress Traffic Classes |
Indicates that this switch supports two priority output queues. |

6.E.2 Port Traffic Class Information
This switch provides two priority levels with Weighted Fair Queuing for port egress. This means that any frames with a default or user priority from 0~3 are sent to the low priority queue "0" while those from 4~7 are sent to the high priority queue "1" as shown in the following screen.
Parameter |
Description |
Port |
Numeric identifier for switch port. |
User Priority |
Shows that user priorities 0~3 specify the low priority queue and 4~7 specify the high priority queue. |
Class Range |
The priority queue classes available on this switch. |
You can use the VLAN configuration menu to assign any port on the switch to any of up to 255 LAN groups. In conventional networks with routers, broadcast traffic is split up into separate domains. Switches do not inherently support broadcast domains. This can lead to broadcast storms in large networks that handle a lot of NetBeui or IPX traffic. By using IEEE 802.1Q compliant VLANs, you can organize any group of network nodes into separate broadcast domains, confining broadcast traffic to the originating group. This also provides a more secure and cleaner network environment. For more information on how to use VLANs, refer to "Virtual LANs". The VLAN configuration screens are described in the following sections.
The VLAN Basic Information screen displays basic information on the VLAN type supported by this switch.
Parameter |
Description |
VLAN Version Number |
The VLAN version used by this switch as specified in the IEEE 802.1Q standard. |
MAX VLAN ID |
Maximum VLAN ID recognized by this switch. |
MAX Supported VLANs |
Maximum number of VLANs that can be configured on this switch. |
Current Number of VLANs Configured |
The number of VLANs currently configured on this switch. |
This screen shows the current port members of each VLAN and whether or not the port supports VLAN tagging. Ports assigned to a large VLAN group that crosses several switches should use VLAN tagging. However, if you just want to create a small port-based VLAN for one or two switches, you can assign ports to the same untagged VLAN. The current configuration is shown in the following screen.
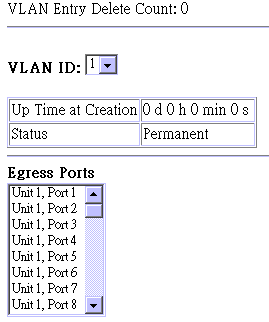
Parameter |
Description |
VLAN Entry Delete Count |
The number of times a VLAN entry has been deleted from this table. |
VLAN ID |
The ID for the VLAN currently displayed. |
Up Time at Creation |
The value of System Up Time (sysUpTime) when this VLAN was created. |
Status |
Shows how this VLAN was added to the
switch. |
Egress Ports |
Shows the ports which have been added to the displayed VLAN group. |
Untagged Ports |
Shows the untagged VLAN port members. |
Use this screen to create or remove VLAN groups.
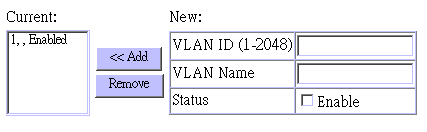
Parameter |
Description |
Current |
Lists all the current VLAN groups created
for this system. Up to 255 VLAN groups can be defined. |
New |
Allows you to specify the name and numeric identifier for a new VLAN group. (The VLAN name is only used for management on this system; it is not added to the VLAN tag.) |
Status |
Enables/disables the specified VLAN. |
Add |
Adds a new VLAN group to the current list. |
Remove |
Removes a VLAN group from the current
list. |
Use this screen to modify the
settings for an existing VLAN. You can add/delete port members for a VLAN from
any unit in the stack. (Note that VLAN1 is fixed as an untagged VLAN containing
all ports in the stack, and cannot be modified via this screen.)
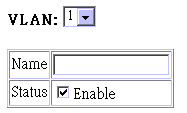
Parameter |
Description |
VLAN |
The ID for the VLAN currently displayed. |
Name |
A user-specified symbolic name for this
VLAN. |
Status |
Enables/disables the specified VLAN. |
Use the following menu to add or remove a port to the displayed VLAN group. As you can see from this example, all ports are included in VLAN 1 by default.

Parameter |
Description |
Egress Ports |
Adds ports to the specified VLAN. |
Use the menu shown below to prevent a port from being dynamically added to the displayed VLAN group through GVRP

Parameter |
Description |
Forbidden Egress Ports |
Prevents a port from being automatically added to this VLAN via GVRP. Note that GVRP is not supported by the current firmware version. |
Use the menu shown below to assign ports to the specified VLAN group as an IEEE 802.1Q tagged or untagged port. Assign ports as tagged if they are connected to 802.1Q VLAN compliant devices, or untagged if they are connected to VLAN-unaware devices.
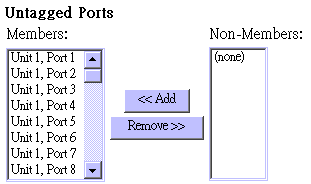
Parameter |
Description |
Untagged Ports |
Adds an authorized egress port to the displayed VLAN as an untagged port. |
NOTES: |
If a removed port is no longer assigned to any other group as an untagged port, it will automatically be assigned to VLAN group 1 as untagged. |
6.F.5 VLAN Static Membership by Port
Use the screen shown below to assign VLAN groups to the selected port. To perform detailed port configuration for a specific VLAN, use the VLAN Static Table.

Parameter |
Description |
Port Number |
Port number on the switch selected from the upper display panel. |
Add/Remove |
Add or remove selected VLAN groups for the port indicated in the Port Number field. |
Use this screen to configure port-specific settings for IEEE 802.1Q VLAN features.
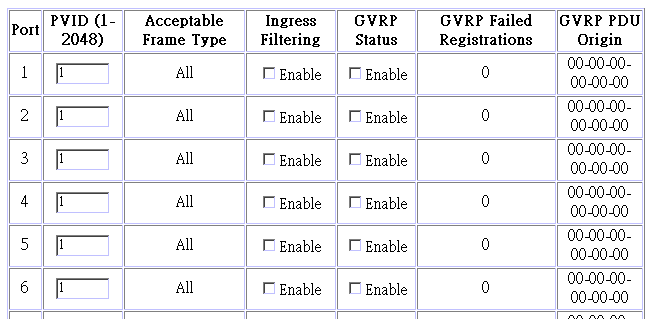
Parameter |
Description |
PVID |
The VLAN ID assigned to untagged frames received on this port. Use the PVID to assign ports to the same untagged VLAN. |
Acceptable Frame Type |
This switch accepts "All" frame types, including VLAN tagged or VLAN untagged frames. Note that all VLAN untagged frames received on this port are assigned to the PVID for this port. |
Ingress Filtering |
If set to "True" incoming frames for VLANs which do not include this port in their member set will be discarded at the inbound port. |
GVRP Status* |
Enables or disables GVRP for this port.
When disabled, any GVRP packets received on this port will be
discarded and no GVRP registrations will be propagated from
other ports. |
GVRP Failed Registrations* |
The total number of failed GVRP registrations, for any reason, on this port. |
GVRP Last PDU Origin* |
The Source MAC Address of the last GVRP message received on this port. |
Multicasting is used to support real-time applications such as video conferencing or streaming audio. A multicast server does not have to establish a separate connection with each client. It merely broadcasts its service to the network, and any hosts which want to receive the multicast register with their local multicast switch/ router. Although this approach reduces the network overhead required by a multicast server, the broadcast traffic must be carefully pruned at every multicast switch/router it passes through to ensure that traffic is only passed on the hosts which subscribed to this service. This switch uses IGMP (Internet Group Management Protocol) to query for any attached hosts who want to receive a specific multicast service. The switch looks up the IP Multicast Group used for this service and adds any port which received a similar request to that group. It then propagates the service request on to any neighboring multicast switch/router to ensure that it will continue to receive the multicast service. (For more information, see "IGMP Protocol".)
This protocol allows a host to inform its local switch/router that it wants to receive transmissions addressed to a specific multicast address group. Use the IGMP Configuration screen to set key parameters for multicast filtering as shown below.
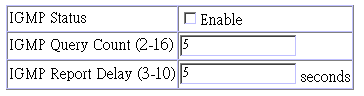
Parameter |
escription |
IGMP Status |
If enabled, the switch will monitor network traffic to determine which hosts want to receive multicast traffic. |
Act as IGMP Querier* |
If enabled, the switch can serve as the "Querier" which is responsible for asking hosts is they want to receive multicast traffic. |
IGMP Query Count* |
The maximum number of queries issued for which there has been no response before the switch takes action to solicit reports. |
IGMP Report Delay* |
The time (in minutes) between receiving an IGMP Report for an IP multicast address on a port before the switch sends an IGMP Query out that port and removes the entry from its list. |
* IGMP Query is not available
in the current firmware release.
NOTES: |
The default values are indicated in the sample screen |
6.G.2 IP Multicast Registration Table
Use the IP Multicast Registration Table to display all the multicast groups active on this switch, including multicast IP addresses and the corresponding VLAN ID.

Parameter |
Description |
VLAN ID |
VLAN ID assigned to this multicast group. |
Multicast IP Address |
IP address for specific multicast services. |
Learned by |
Indicates the manner in which this address was learned: Dynamic or IGMP. |
Multicast Group Port Lists |
The switch ports registered for the indicated multicast service. |
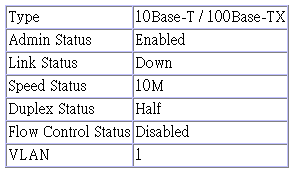
The Port Information screen displays the port status, link state, the communication speed and duplex mode, as well as the flow control in use. To change any of the port settings, use the Port Configuration menu. The parameters are shown in the following figure and table.
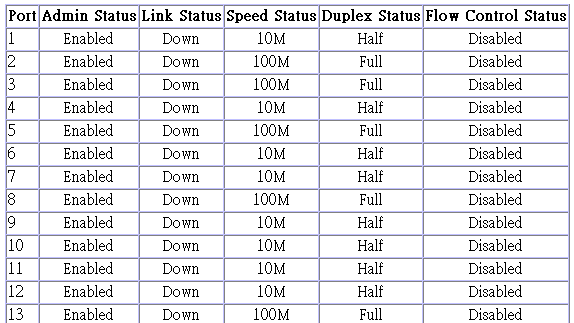
Parameter |
Description |
Admin Status |
Shows if the port is enabled or not. |
Link Status |
Indicates if the port has a valid connection to an external device. |
Speed Status |
Shows the port speed (10M, 100M or 1000M). |
Duplex Status |
Displays the current duplex mode. |
Flow Control Status |
Shows the flow control type in use. Flow control can eliminate frame loss by ¤blocking?traffic from end stations connected directly to the switch. Back pressure is used for half duplex and IEEE 802.3x for full duplex. Note that flow control should not be used if a port is connected to a hub. |
Use the Port Configuration menu to configure any port on the switch.

Parameter |
Default |
Description |
Flow Control (on all ports) |
Disabled |
See "Flow Control Status" in this table. |
Admin Status |
Enable |
Allows you to disable a port due to abnormal behavior, and then re-enable it after the problem has been resolved. You may also disable a port for security reasons. |
Duplex Status |
Auto-Negotiation |
Negotiation Used to set the current port
speed, duplex mode, flow control, and auto-negotiation. |
Flow Control |
Disabled |
Used to enable or disable flow control. Flow control can eliminate frame loss by "blocking" traffic from end stations or segments connected directly to the switch when its buffers fill. Back pressure is used for half duplex and IEEE 802.3x for full duplex. Note that flow control should not be used if a port is connected to a hub. |
NOTES: |
100BASE-FX
is fixed at 100 Mbps, full-duplex. |
6.I Using a Port Mirror for Analysis
You can mirror traffic from any source port to a target port for real-time analysis. You can then attach a logic analyzer or RMON probe to the target port and study the traffic crossing the source port in a completely unobtrusive manner. When mirroring port traffic, note that the target port must be included in the same VLAN as the source port. (See VLAN Static List)
You can use the port mirror configuration screen to designate a single port pair for mirroring as shown below.
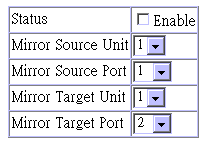
Parameter |
Description |
Status |
Enables/disables port mirroring. |
Mirror Source Unit |
The switch containing the mirror source port. |
Mirror Source Port |
The port whose traffic will be monitored. |
Mirror Target Unit |
The switch containing the mirror target port. |
Mirror Target Port |
The port that will duplicate or ¤mirror?all the traffic happening on the monitored port. |
Port trunks can be used to increase the bandwidth of a network connection or to ensure fault recovery. You can configure up to four trunk connections (combining 2~4 ports into a fat pipe) between any two switches. However, before making any physical connections between devices, use the Trunk Configuration menu to specify the trunk on the devices at both ends.
When using a port trunk, note that:
Use the Port Trunking Configuration screen to set up port trunks as shown below:
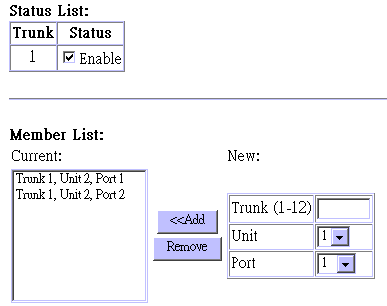
Parameter |
Description |
Trunk |
A unique identifier for this trunk. You can configure up to four trunks per switch. |
Status |
Enables or disables the displayed trunk. |
Member List |
You can create up to 16 trunks for the entire stack by specifying the trunk identifier, switch unit and port number, and then pressing the "Add" button. Each trunk can contain from 2 to 4 ports. |
The RJ-45 ports used for one side of a trunk
must all be on the same internal switch chip. The port groups permitted include:
Switch Model |
Group 1 |
Group 2 |
Group 3 |
SGSW-2403 |
1,2,3,4,13,14,15,16 |
5,6,7,8,17,18,19,20 |
9,10,11,12,21,22,23,24 |
The 100BASE-FX fiber ports used for one side
of a trunk must all be on the same module. However, the 1000BASE-SX ports used
for one side of a trunk may be on any switch in the stack, or both on the same
switch if used standalone.
Media Module |
|
100BASE-FX |
Any ports on a single module |
1000BASE-SX |
Up to four Gigabit ports from any switch in the stack, or both Gigabit ports on two modules installed in a standalone switch. |
For example, when using Gigabit ports to form
a trunk within a stack, the Gigabit ports will all be at Port 25. In this case,
you could specify a trunk group consisting of: (Unit1-Port25, Unit2-Port25,
Unit3-Port25, Unit4-Port25),
or two trunks consisting of: (Unit1-Port25, Unit2-Port25) and (Unit3-Port25,
Unit4-Port25).
Use the Port Statistics menu to display Etherlike or RMON statistics for any port on the switch. The statistics displayed are indicated in the following figure and table.
Etherlike Statistics display key statistics from the Ethernet-like MIB for each port. Error statistics on the traffic passing through each port are displayed. This information can be used to identify potential problems with the switch (such as a faulty port or unusually heavy loading). Values displayed have been accumulated since the last system reboot.
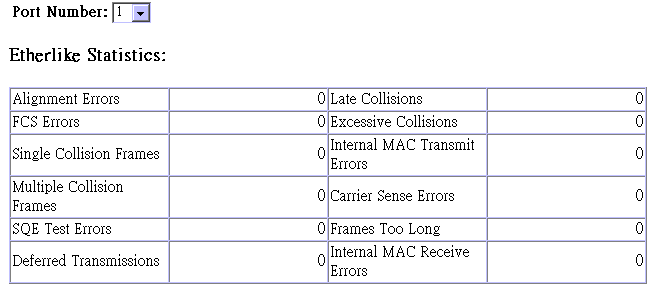
Parameter |
Description |
Alignment Errors |
The number of alignment errors (mis-synchronized data packets). |
FCS Errors |
The number of frames received that are an integral number of octets in length but do not pass the FCS check. |
Single Collision Frames* |
The number of successfully transmitted frames for which transmission is inhibited by exactly one collision. |
Multiple Collision Frames* |
A count of successfully transmitted frames for which transmission is inhibited by more than one collision. |
SQE Test Errors* |
A count of times that the SQE TEST ERROR message is generated by the PLS sublayer. |
Deferred Transmissions* |
A count of frames for which the first transmission attempt on a particular interface is delayed because the medium was busy. |
Late Collisions |
The number of times that a collision is detected later than 512 bit-times into the transmission of a packet. |
Excessive Collisions* |
The number of frames for which transmission failed due to excessive collisions. |
Internal Mac Transmit Errors* |
The number of frames for which transmission failed due to an internal MAC sublayer transmit error. |
Carrier Sense Errors* |
The number of times that the carrier sense condition was lost or never asserted when attempting to transmit a frame. |
Frames Too Long |
The number of frames received that exceed the maximum permitted frame size. |
Internal Mac Receive Errors* |
Errors* The number of frames for which reception failed due to an internal MAC sublayer receive error. |
* The reported values will always be zero because these statistics are not supported by the internal chip set used in this switch.
NOTES: |
Statistics are automatically refreshed every 60 seconds. |
RMON Statistics display key statistics for each port or media module from RMON group 1. (RMON groups 2, 3 and 9 can only be accessed using SNMP management software such as AccView.) The following screen displays overall statistics on traffic passing through each port. RMON statistics provide access to a broad range of statistics, including a total count of different frame types passing through each port. Values displayed have been accumulated since the last system reboot.
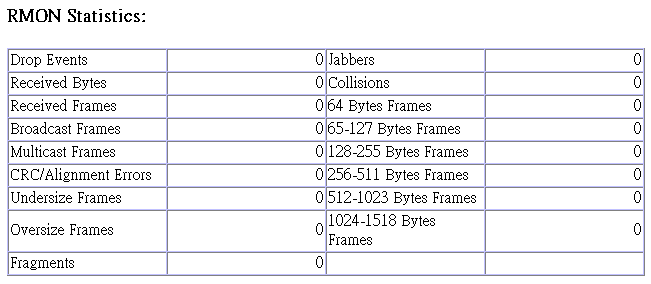
Parameter |
Description |
Drop Events |
The total number of events in which packets were dropped due to lack of resources. |
Received Bytes |
Total number of bytes of data received on the network. This statistic can be used as a reasonable indication of Ethernet utilization. |
Received Frames |
The total number of frames (bad, broadcast and multicast) received. |
Broadcast Frames |
The total number of good frames received that were directed to the broadcast address. Note that this does not include multicast packets. |
Multicast Frames |
The total number of good frames received that were directed to this multicast address. |
CRC/Alignment Errors |
The number of CRC/alignment errors (FCS or alignment errors). |
Undersize Frames |
The total number of frames received that were less than 64 octets long (excluding framing bits, but including FCS octets) and were otherwise well formed. |
Oversize Frames |
The total number of frames received that were longer than 1518 octets (excluding framing bits, but including FCS octets) and were otherwise well formed. |
Fragments |
The total number of frames received that were less than 64 octets in length (excluding framing bits, but including FCS octets) and had either an FCS or alignment error. |
Jabbers |
The total number of frames received that were longer than 1518 octets (excluding framing bits, but including FCS octets), and had either an FCS or alignment error. |
Collisions |
The best estimate of the total number of collisions on this Ethernet segment. |
64 Byte Frames |
The total number of frames (including bad packets) received and transmitted that were 64 octets in length (excluding framing bits but including FCS octets). |
65-127 Byte Frames |
The total number of frames (including bad packets) received and transmitted that were between 65 and 127 octets in length inclusive (excluding framing bits but including FCS octets). |
128-255 Byte Frames |
The total number of packets (including bad packets) received and transmitted that were between 128 and 255 octets in length inclusive (excluding framing bits but including FCS octets). |
256-511 Byte Frames |
The total number of packets (including bad packets) received and transmitted that were between 256 and 511 octets in length inclusive (excluding framing bits but including FCS octets). |
512-1023 Byte Frames |
The total number of packets (including bad packets) received and transmitted that were between 512 and 1023 octets in length inclusive (excluding framing bits but including FCS octets). |
1024-1518 Byte Frames |
The total number of packets (including bad packets) received and transmitted that were between 1024 and 1518 octets in length inclusive (excluding framing bits but including FCS octets). |
NOTES: |
Statistics are automatically refreshed every 60 seconds. |
|
|
|
Copyright (c) 2001, Planet Technology Corp. |